Enterprise
Enterprise
Enterprise
Security by design, engineered for enterprise scale
Least privilege access, comprehensive data encryption, and PHI minimization baked into every workflow and decision.
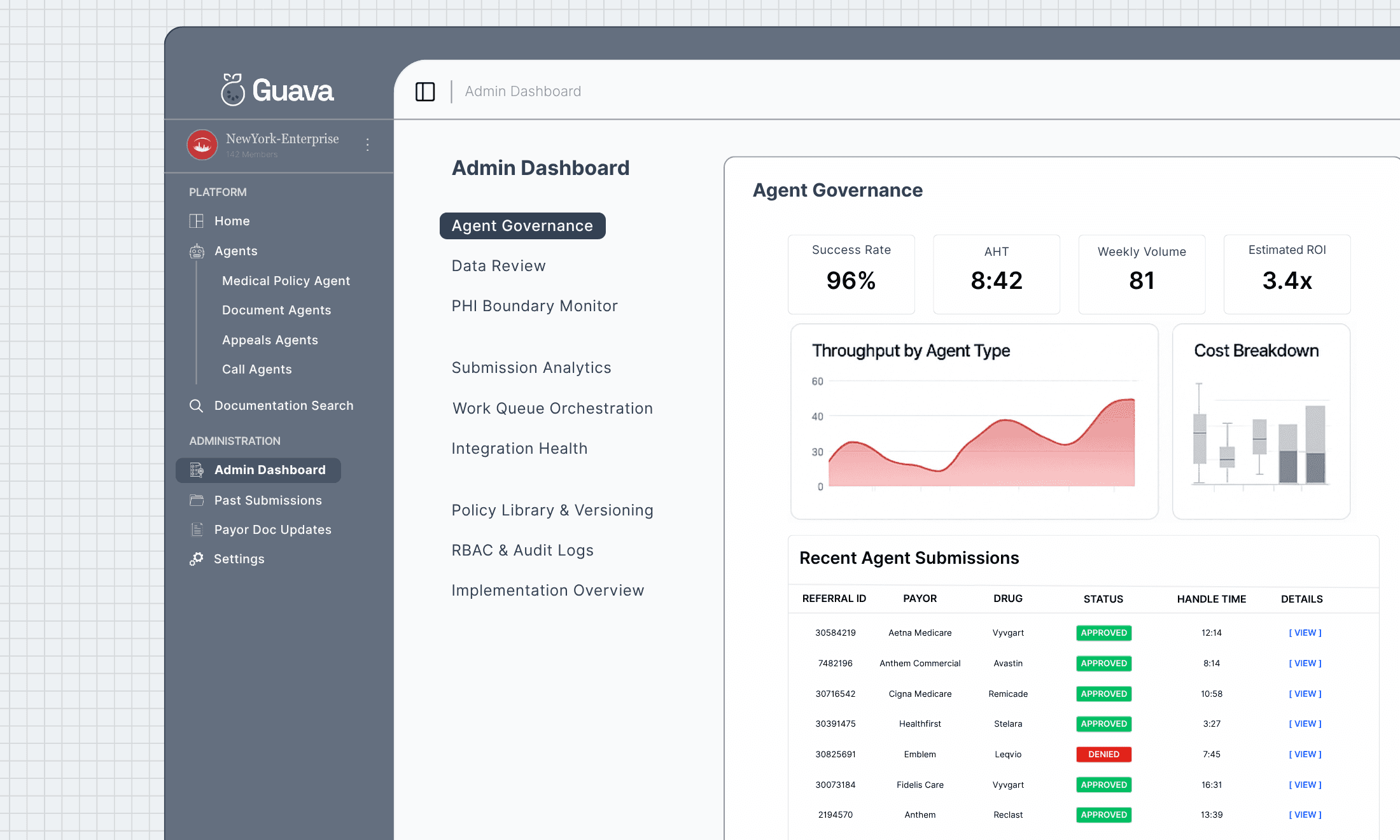
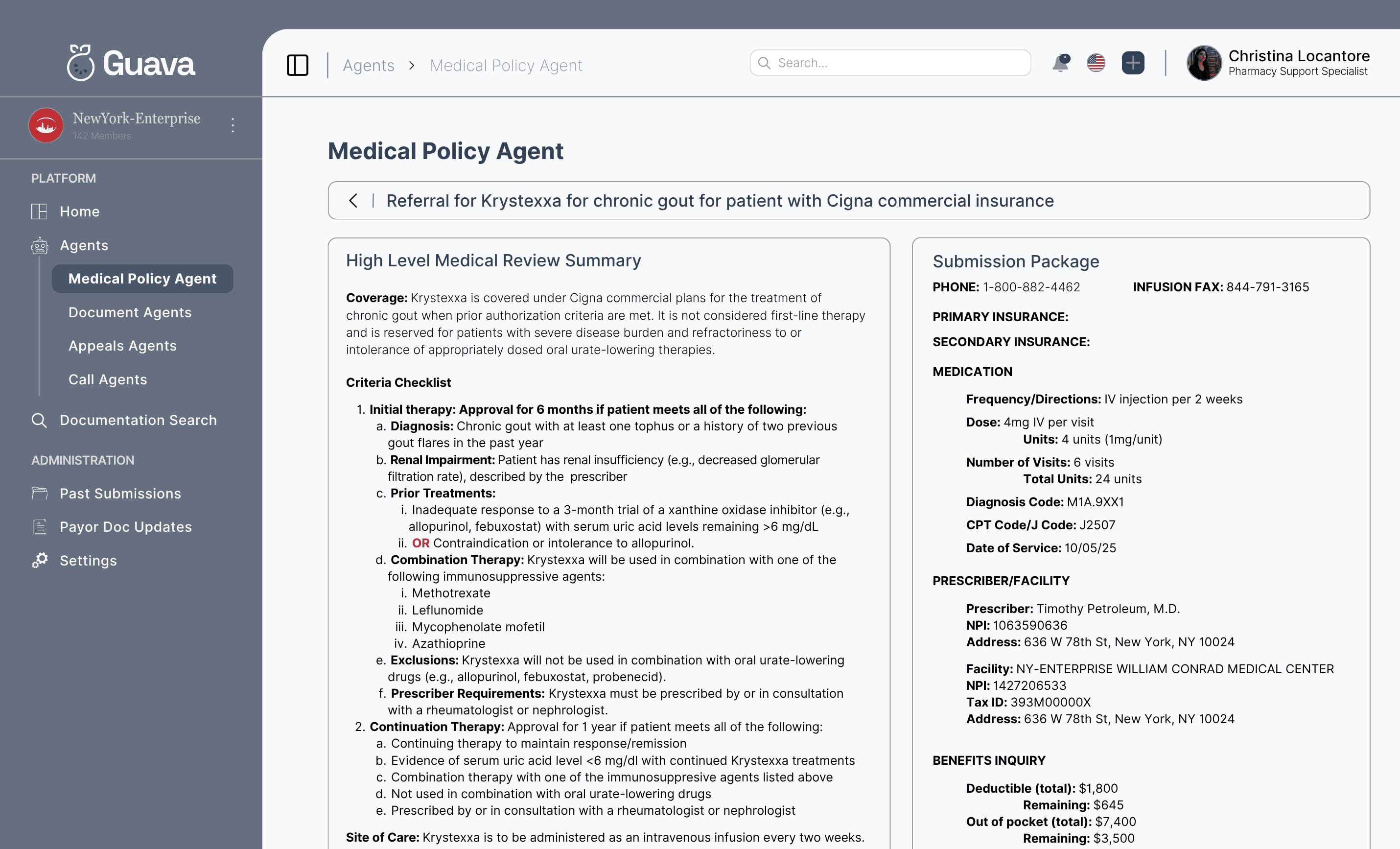
Comprehensive Oversight
Monitor both your organization as well as agent performance with comprehensive analytics for KPIs and performance across both human and agentic workflows
Track Features
Oversee and use the same tools your specialists use with advanced insights, providing an unmatched custom experience in choosing how you implement
Data Governance
Access comprehensive overviews for data processing as well as data usage across your organization at the click of a button.



Oversight
Monitor both your organization as well as agent performance with comprehensive analytics for KPIs and performance across both human and agentic workflows
Track
Oversee and use the same tools your specialists use with advanced insights, providing an unmatched custom experience in choosing how you implement
Governance
Access comprehensive overviews for data processing as well as data usage across your organization at the click of a button.



Comprehensive Oversight
Monitor both your organization as well as agent performance with comprehensive analytics for KPIs and performance across both human and agentic workflows
Track Features
Oversee and use the same tools your specialists use with advanced insights, providing an unmatched custom experience in choosing how you implement
Data Governance
Access comprehensive overviews for data processing as well as data usage across your organization at the click of a button.
Our Compliance Pillars
Our Compliance Pillars
Our Compliance Pillars
Guava adheres to six core pillars of compliance
Every automation is built to be able to comprehensively handle all of your workflows, no matter the complexity. All while maintaining rigorous enterprise-grade security, transparency, and auditability.
HIPAA Safe Harbor Alignment
What it means to you: we adhere strictly to HIPAA's de-identification and Safe Harbor principles
What it means to us: all ingestion and automation modules exclude the 18 protected identifiers defined under §164.514(b)
SOC-2 Mapped Controls
What it means to you: internal security and change management processes follow SOC-2 CC1-CC8 domains
What it means to us: access logging, encryption, key rotation, and audit events are continuously monitored
Data Minimization by Design
What it means to you: Guava processes only payor and policy data, not patient records
What it means to us: every data path is validated against an allow-list scheuma before execution
Zero Required EHR Connectivity
What it means to you: no required EHR integration or PHI transfer
What it means to us: all workflows operate from structured payor documentation and administrator input only
AI Governance & Human Oversight
What it means to you: every agent action is logged and reviewable
What it means to us: human-in-the-loop checkpoints ensure transparency and override capability
Encryption and Integrity
What it means to you: confidentiality and integrity throughout the entire lifecycle
What it means to us: AES-256 encryption for data at rest; SHA-256 hashing for integrity and detailed audit trails
HIPAA Safe Harbor Alignment
What it means to you: we adhere strictly to HIPAA's de-identification and Safe Harbor principles
What it means to us: all ingestion and automation modules exclude the 18 protected identifiers defined under §164.514(b)
SOC-2 Mapped Controls
What it means to you: internal security and change management processes follow SOC-2 CC1-CC8 domains
What it means to us: access logging, encryption, key rotation, and audit events are continuously monitored
Data Minimization by Design
What it means to you: Guava processes only payor and policy data, not patient records
What it means to us: every data path is validated against an allow-list scheuma before execution
Zero Required EHR Connectivity
What it means to you: no required EHR integration or PHI transfer
What it means to us: all workflows operate from structured payor documentation and administrator input only
AI & Human Oversight
What it means to you: every agent action is logged and reviewable
What it means to us: human-in-the-loop checkpoints ensure transparency and override capability
Encryption and Integrity
What it means to you: confidentiality and integrity throughout the entire lifecycle
What it means to us: AES-256 encryption for data at rest; SHA-256 hashing for integrity and detailed audit trails
HIPAA Safe Harbor Alignment
What it means to you: we adhere strictly to HIPAA's de-identification and Safe Harbor principles
What it means to us: all ingestion and automation modules exclude the 18 protected identifiers defined under §164.514(b)
SOC-2 Mapped Controls
What it means to you: internal security and change management processes follow SOC-2 CC1-CC8 domains
What it means to us: access logging, encryption, key rotation, and audit events are continuously monitored
Data Minimization by Design
What it means to you: Guava processes only payor and policy data, not patient records
What it means to us: every data path is validated against an allow-list scheuma before execution
Zero Required EHR Connectivity
What it means to you: no required EHR integration or PHI transfer
What it means to us: all workflows operate from structured payor documentation and administrator input only
AI Governance & Human Oversight
What it means to you: every agent action is logged and reviewable
What it means to us: human-in-the-loop checkpoints ensure transparency and override capability
Encryption and Integrity
What it means to you: confidentiality and integrity throughout the entire lifecycle
What it means to us: AES-256 encryption for data at rest; SHA-256 hashing for integrity and detailed audit trails
Guava was built on a simple principle, which is that security and compliance are embedded and not added.
Every one of our modules, APIs, and AI agents are built around data minimization and AI governance.
Guava was built on a simple principle, which is that security and compliance are embedded and not added.
Every one of our modules, APIs, and AI agents are built around data minimization and AI governance.
Guava was built on a simple principle, which is that security and compliance are embedded and not added.
Every one of our modules, APIs, and AI agents are built around data minimization and AI governance.
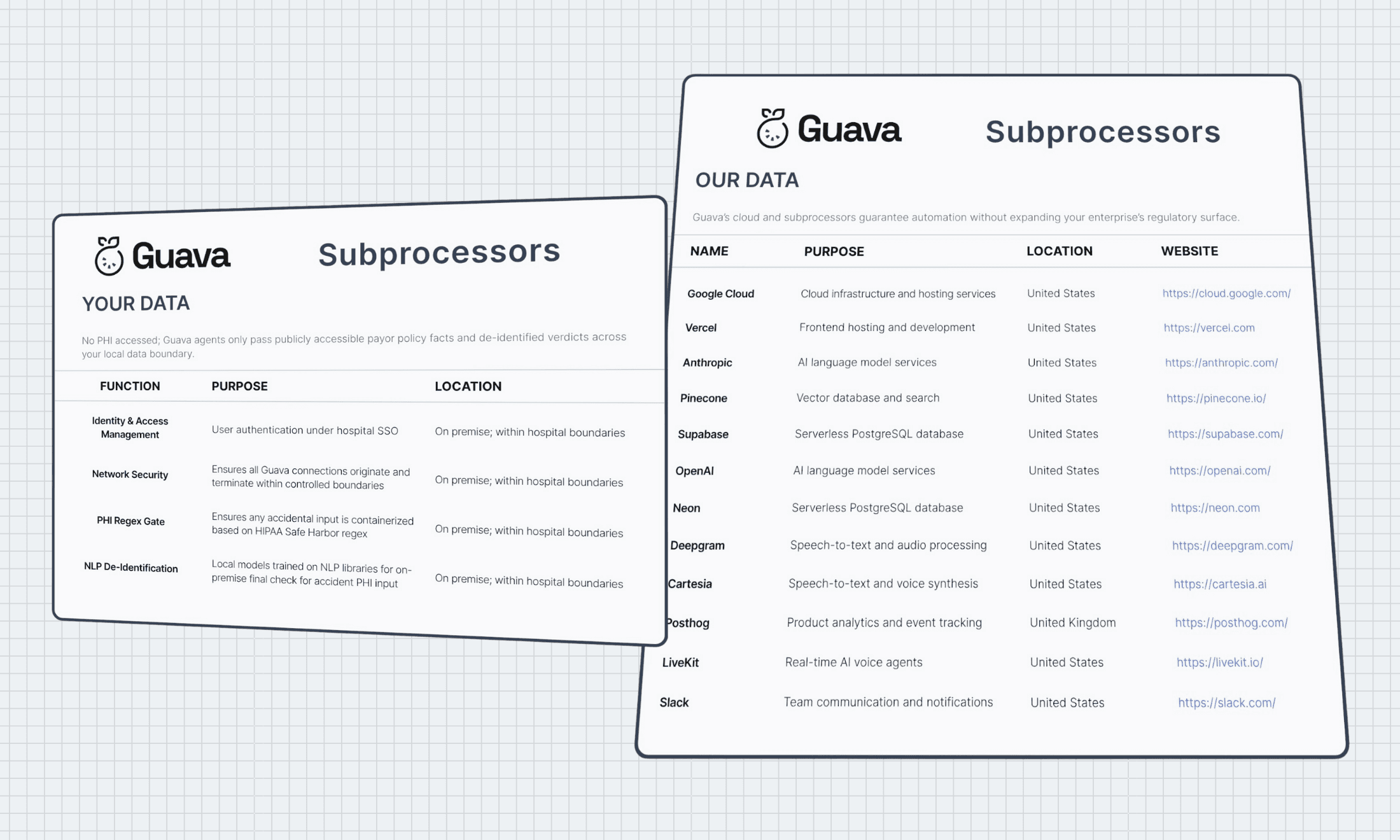
For legal, information security, and procurement teams, we offer a detailed compliance packet including information on:
•. SOC-2 Control Mapping
•. HIPAA Safe Harbor Attestation
•. Our subprocessor DPAs
• Overview of our NLP and de-idenitification architecture
• Summary of Data Retention and Access Policy
Please contact security@guavamedical.ai for any and all inquiries. Include "Compliance Packet" in subject line to request a detailed authorized copy provided under signed NDA.
For legal, information security, and procurement teams, we offer a detailed compliance packet including information on:
•. SOC-2 Control Mapping
•. HIPAA Safe Harbor Attestation
•. Our subprocessor DPAs
• Overview of our NLP and de-idenitification architecture
• Summary of Data Retention and Access Policy
Please contact security@guavamedical.ai for any and all inquiries. Include "Compliance Packet" in subject line to request a detailed authorized copy provided under signed NDA.